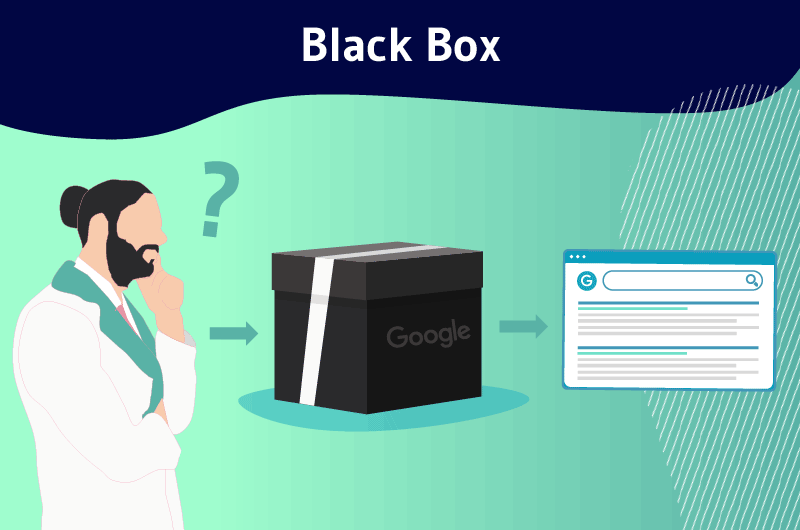
A Black Box is a complex computer program whose inputs and outputs can be observed, but whose internal processes are not accessible due to their confidential nature.
In the world of SEO, the notion of Black Box is an abstract concept generally used to designate software whose processes are not known to the general public.
For a better understanding of this intriguing concept, we’re going to study it in great detail. The aim here is to provide clear and satisfactory answers to all the questions and concerns raised by the subject.
- What exactly is a Black Box?
- Which disciplines use the Black Box concept?
- What do we know about Google’s Black Box algorithm?
- What impact does the Black Box algorithm have on SEO?
- How can I get past Google’s Black Box?
This introduction to the Black Box provides an overview of its history, key definitions, various applications and SEO implications.
Pay attention!
Chapter 1: Black Box theory in detail
Black Box systems theory is a term often used in the scientific world, in computer science and in high-level engineering.
1-1- History of the Black Box: different references over time
The term Black Box, in the modern sense we know it today, was introduced into the English language around 1945. But it’s important to note that the concept was officially mentioned several years earlier.
Indeed, Wilhelm Cauer is credited with the first reference to systems as Black Boxes. In his work, published in its most elaborate form in 1941, the German mathematician likened electrical circuits to Black Boxes.
An expression probably borrowed from the military world and used at the time in telecommunications to designate apprehended enemy devices that could not be dismantled for fear of being booby-trapped.
These enemy technologies had to be examined and studied without their internal components being visible and accessible.
But long before Wilhelm Cauer, scientists such as Vitold Belevitch and his contemporaries were already arguing in 1921 that the operation of electrical networks with two pairs of terminals should not be treated in any other way than as Black Boxes.
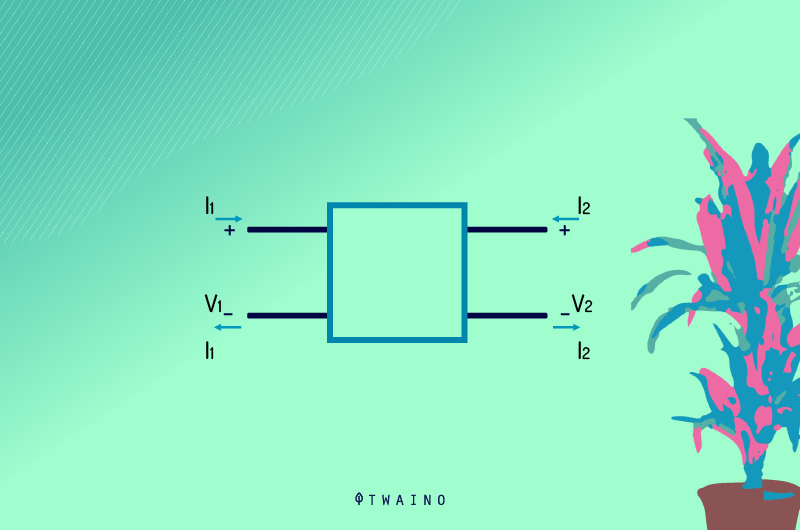
To corroborate these various assertions, numerous studies and comprehensive descriptions of the Black Box would be carried out many years later. Norbert Wiener ‘s rather exhaustive theorization of the principle in 1961 followed Ross Ashby ‘s complete exploration of the Black Box in 1956.
And so it is that Black Box theory has been taken up, studied and perfected again and again by many other scientists, epistemologists and engineers over the years to this day.
1-2- What exactly is a Black Box?
A Black Box is any system, device or object capable of being observed in terms of its transfer characteristics (inputs and outputs), without clear knowledge of its intrinsic organization and operation.
The term therefore represents a device that can be identified solely on the basis of its behavior.
The Black Box principle can be summed up as an opaque box whose contents are invisible or incomprehensible. Incoming stimuli (inputs) are transformed, changed and then presented by unknown mechanisms in the form of more or less different responses (outputs).
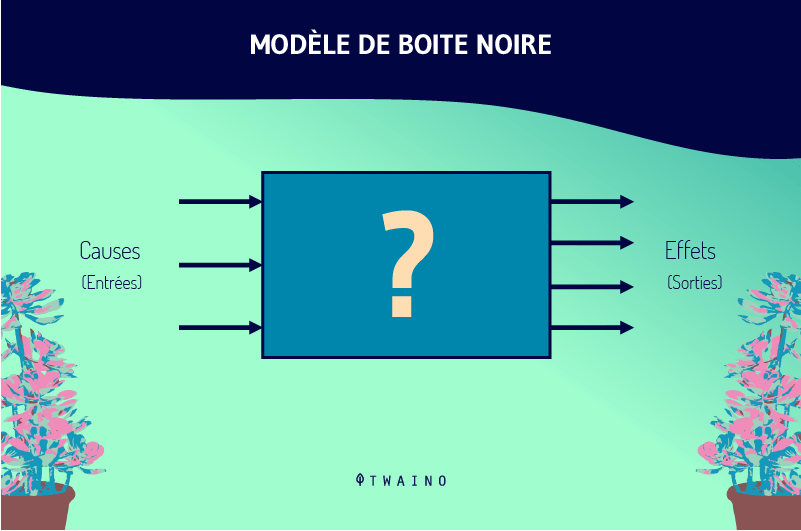
As you can see, the Black Box principle can be applied in almost any field. And with good reason: when it comes to the human brain, computer algorithms or transistors, the notion of the Black Box comes up frequently.
In this case, it refers to the inaccessible or deliberately omitted inner workings that make up these incredible structures.
Of course, the existence of Black Box processes also implies the undeniable existence of White Box processes.
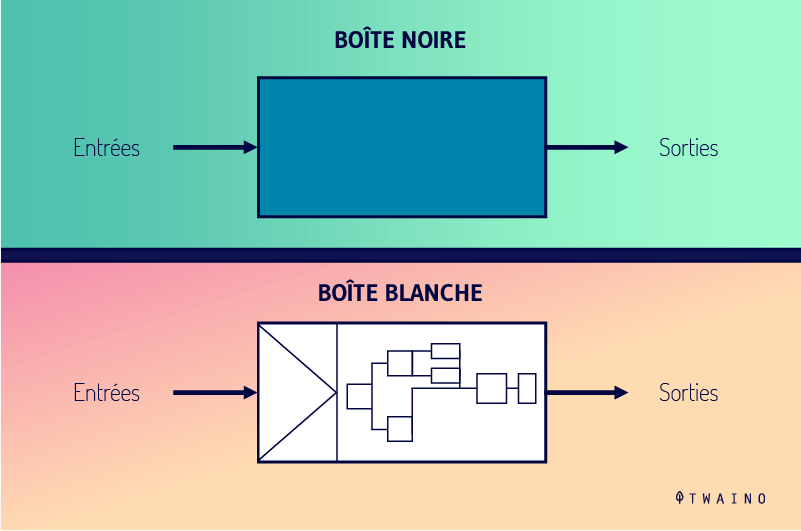
In contrast to the Black Box, White Box or Clear Box systems are transparent in the sense that their inner workings are visible, accessible and comprehensible.
1-3- In concrete terms, how does a Black Box system work?
Like the theory of open systems, to which it is closely related, Black Box theory focuses on the study of input and output flows.
1-3-1- What is an open system?
As opposed to a closed or isolated system, an open system is simply a circuit that interacts in places with the outside world. These interactions are nothing more than exchanges and transfers of data in the form of information, energy or matter, on either side of the system’s boundaries.
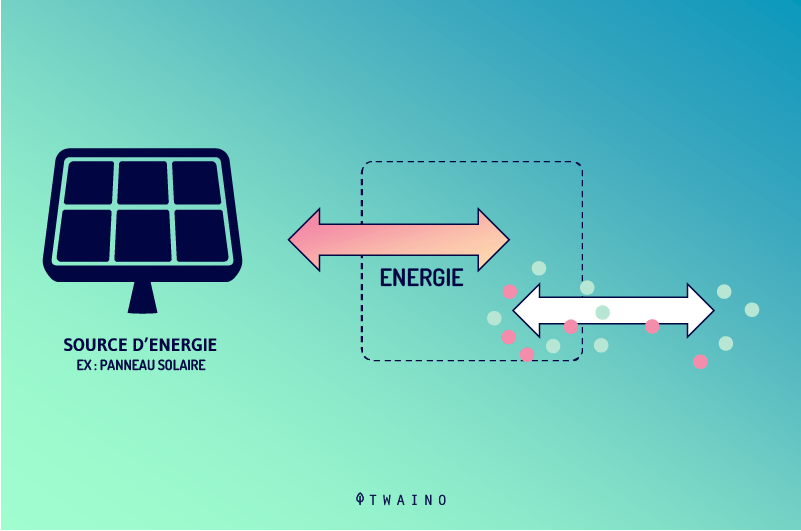
These open-system interactions are also known as input and output flows. By simple analogy, we understand that any Black Box system is an open system. This is perfectly true even if the central element linking inputs and outputs is completely hidden in the case of the Black Box.
1-3-2- Black Box system summary
The analysis of a Black Box system is carried out exclusively by recording and accounting for its visible states (its reactions to stimuli).
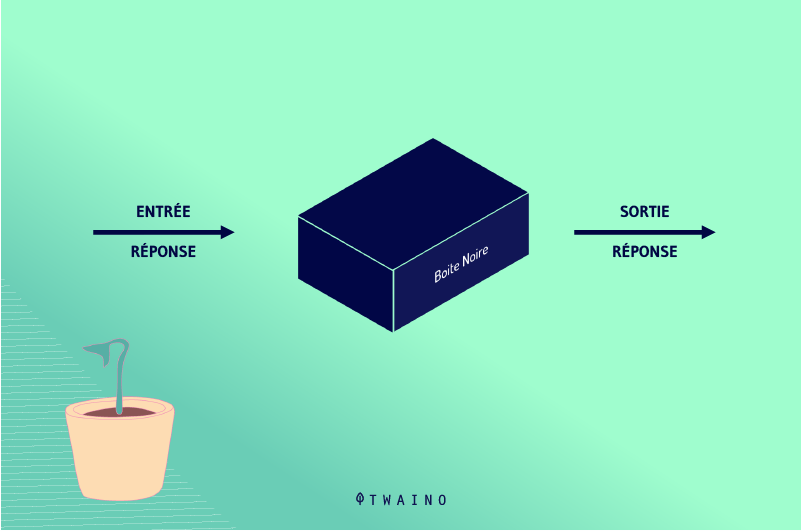
Consequently, the characteristics of a Black Box are deduced only from the angle of its interactions with the environment.
This study approach only highlights the form or limits of the Black Box, whose content remains unknown and misunderstood.
True understanding of a Black Box is based entirely on the hypothesis of a cause-and-effect relationship between stimulus and reaction.
An explanatory principle that holds that the system has observable inputs and outputs, and that the system itself is impenetrable to the observer.
Chapter 2: At the heart of the Black Box by Google algorithm
In line with its outward presentation, Google is certainly the most representative case of how Black Box theory developed and why it looks intriguing.
2-1- How did Google search become a Black Box?
2-1-1- Evolution of Google search
Surfing the web before the advent of Google was a real pain for cybernauts. In those days, the web was synonymous with cluttered portals, unwanted ads and endless spam.
The web giant has established itself in the sector by ensuring clarity, relevance, cleanliness and speed in its search result proposals.
Now a universal directory, Google’s commercial success has given it immeasurable power over the nature and quality of the information we receive.
The search engine doesn’t reveal the technical details of its ranking methods, but it has provided an outline of a process that has the appearance of being simple and fair. Google ranks websites according to relevance and importance. The greater the number of quality backlinks, the more reliable the web page is considered by Google. As a result, it has a better chance of appearing in the search engine’s top results (SERP) and claiming the top spot in the rankings.
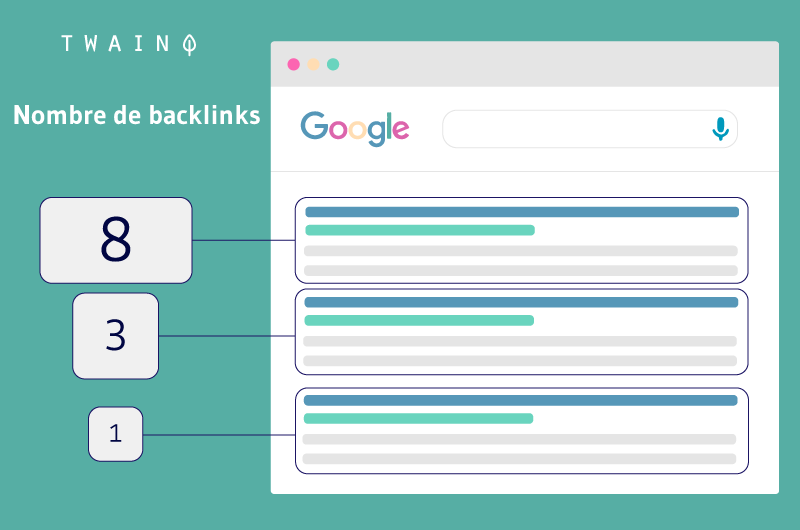
This is the guiding principle behind the famous patented PageRank method, which is responsible for Google’s dazzling exploits.
However, this same method is also the source of many problems. The more the search engine revealed its ranking algorithms, the easier it became to manipulate them. To compensate for various Black Hat SEO practices, the original PageRank patent, initially known to all and sundry, began to be clandestinely modified.
2-1-2- The creation of Google’s Black Box
Major adjustments were made and many complex settings added in secret to combat bad practices tending to circumvent the algorithms:
- links farm;
- content Spinning;
- cloaking;
- duplicate Content;
- and more.
Thus began the race for the methodological secret of search engine optimization. A never-ending game of cat and mouse, which today is the reason why Google and its search technologies appear like a Black Box.
Behind the smooth appearance of Google’s polished interfaces and well-ordered results, lies an impressive network of mechanisms and other defenses in constant flux.
2-1-3- Fallout from the war on spam
The legitimate SEO players responsible for optimizing pages for search engines are caught in the crossfire. And for good reason: they too are being denied access to valuable information about the exact workings of search engine algorithms.
In war as in war, Google uses the never-ending battle against spam and manipulation to justify its neglect of the many controversies surrounding its ranking techniques.
To improve indexing without incurring the “Google Death Penalty” (outright de-indexing of disbelieving sites), SEOs have no choice but to scrutinize all Google’s recommendations and rules.
2-1-4- A rather opaque and sometimes dubious Black Box
The search giant is using its power to extend its services beyond simple web search. An expansion that delights many and gives the company even more clout.
As the world’s leading organizer of information, it’s clearly become very easy for the giant to control information.

Despite its titanic index and incredible performance, Google is becoming less and less trustworthy.
Faced with the omnipotence of the ultimate indexer, many questions and concerns arise. The main one being: is Google using its dominant position in the search world for the public good, or to consolidate its power?
To date, no one can really answer this question. Google takes great care to protect its black box. The company does not hesitate to add thick layers of bureaucratic, technical and contractual opacity at every level, to conceal its procedures, its intentions and even its answers.

For the vast majority of Internet users, the impenetrable nature of Google’s technique makes it a mysterious Black Box, but it’s important not to forget the protective role of this Black Box.
2-2- Black Box and SEO: what’s really going on?
The justified presumption that Google’s algorithm is a Black Box has clearly extended to SEO.
As if to confirm this idea, the multiplicity of organic optimization levers contrasts sharply with the paucity of optimization results.
In other words, it had become difficult, if not impossible, for everyone to understand the causal link between actions taken (inputs) and results obtained (outputs).
How to explain it? Has SEO really become a black box? Many people once thought so.
2-2-1- Is SEO really a Black Box?
Of course, the secret algorithmic workings of search engines are still not accessible. But do we really need access to them when it comes to SEO?
Not really! SEO doesn’t revolve around the search engine itself, but rather around the interactions it has with websites.
For Google, the priority is to continue offering Internet users high-quality, relevant content.
In doing so, it has always made a point of reiterating the standards of SEO regulation and its main ranking criteria.

The search engine’s tried-and-tested guidelines are simple and more than sufficient to enable its users to take their websites to the top of the rankings.
2-2-2- Why is there sometimes a discrepancy between actions taken and results achieved?
When it comes to SEO, there are two main hypotheses to explain this phenomenon.
Either the site’s SEO potential has been incorrectly assessed. In the case of sites designed in disregard of SEO rules, or with a strategy ill-adapted to their objectives, SEO will be poorly executed.
Either, the execution of SEO actions has not been carried out correctly. A faulty plan, problems of prioritization and communication are just some of the factors that can distort a site’s SEO performance.
Most SEO problems are closely linked to the skills of the SEOs.
2-3- What does the future hold for SEA?
With the aim of attracting small and medium-sized businesses, the SEA (Search Engine Advertising) giant has spared no expense in developing Google Ads, its advertising jewel.
Over the years, Google has simplified a number of practices as far as possible. Techniques that were previously known and mastered only by specialized agencies are now within everyone’s reach.
The company has gone so far as to ask advertisers to trust its algorithm to automatically manage all actions that used to be manual.
Google’s flagship advertising platform is now likened to a Black Box.

The search engine’s advertising solution gives SEA protagonists less and less latitude in setting up Ads campaigns. Google Analytics-Adwords now operates in a closed circuit. The challenge now is to guide Google’s secret algorithms towards the advertiser’s business objectives.
The Black Box theory is now used as a real business strategy by the search engine and its peers.
Despite this automation of ATS, the role of ATS experts is as important as ever. Better still, it’s evolving.
Yes, the old trading-buying logic is now obsolete. Rather than simply choosing CPCs (Cost Per Click) associated with keywords, SEA consultants are now called upon to carry out essential reverse-engineering work.
- PerformAB testing to optimize audience typologies;
- Analyze the functioning of automatic bidding tools for better calibration;
- Analyze SEA traffic ( bounce rates) and record the campaign’s share of the conversion tunnel;
- And much more.
2-4- Machine learning to get past the Black Box
2-4-1- What is machine learning?
Machine learning is an important component of the field of data science.
It is a section of AI (Artificial Intelligence) and computer science that essentially deals with the use of data and algorithms to reproduce the way humans learn, progressively improving its accuracy.
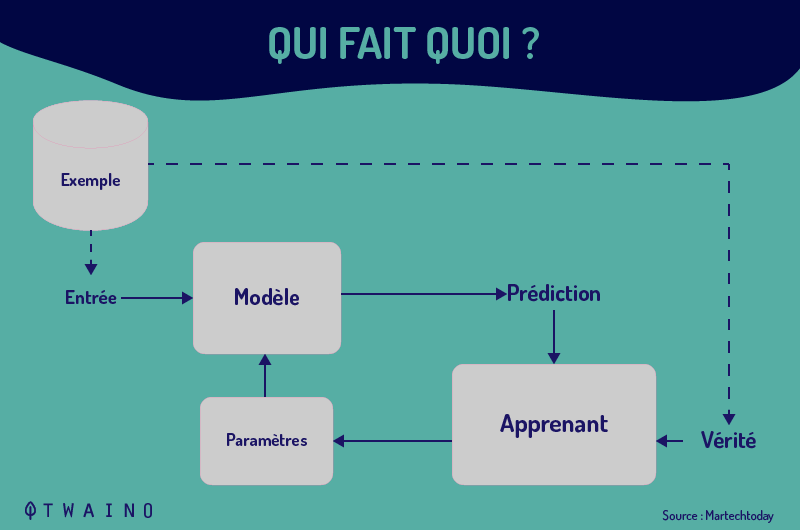
Using statistical methods, algorithms are designed to make classifications or predictions, by identifying key information in data mining projects.
This information then stimulates decision-making within applications and companies, ideally impacting key growth indicators.
2-4-2- A tool and an effective way to bypass the Google Black Box
With machine learning, data collected on search engine behavior is used to discover data trends. These trends can then be used to develop more effective SEO strategies.
To decipher the Black Box, many tools such as ranking trackers had been initiated, but were quickly surpassed by machine learning tools.

Indeed, machine learning in this context involves studying search engine algorithms to decipher their inner workings.
However, this solution for seeing through the Black Box needs to be handled with care.
Since it could expose the web giant’s algorithms, this approach leaves them vulnerable. With the wrong intentions, it could be used to introduce spam and malware.
Is it really worth revealing the contents of Google’s Black Box?
Chapter 3: The Black Box: a truly ubiquitous and polymorphous concept
By now, the Black Box is a well-known term that can be applied to a number of disciplines (IT, human science, economics, etc.). Of course, each of these applications has its own specificities.
3-1- In computer programming and software engineering
As stipulated by the Black Box theory, the term Black Box is used in computer science to verify the output of a program. It is used to ensure that feedback matches input, without ever examining the program itself.
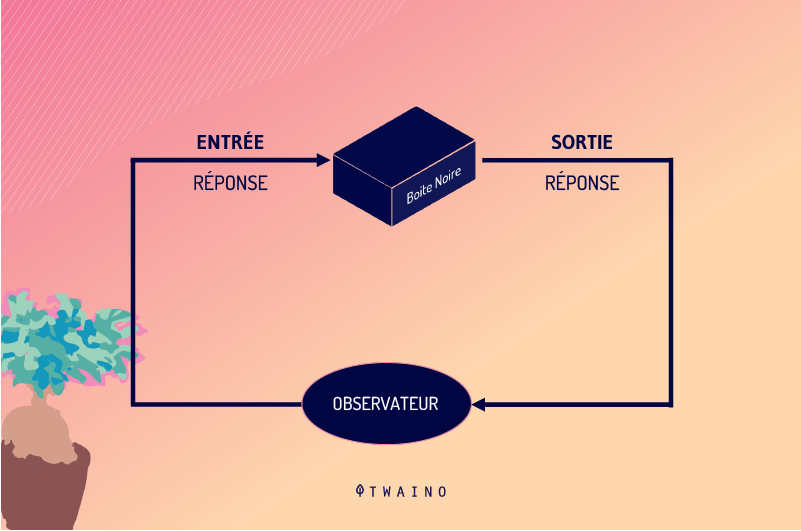
Here, more than an observer, the agent in charge of the study can participate in the experiment by determining and controlling the inputs.
Furthermore, from a user’s point of view, the internal workings of a program are considered Black Box for two reasons. Either because the program is closed-source. Or, because there is no need to examine it (routine use).
3-1-1- Black Box testing
A Black-Box test evaluates software functionality exclusively from the outside, without looking at the internal structures that generate responses to test events (the inputs).
In line with Black Box systems theory, even if the internal workings of the application are visible and understandable during inspection, the tester deliberately chooses to ignore them.
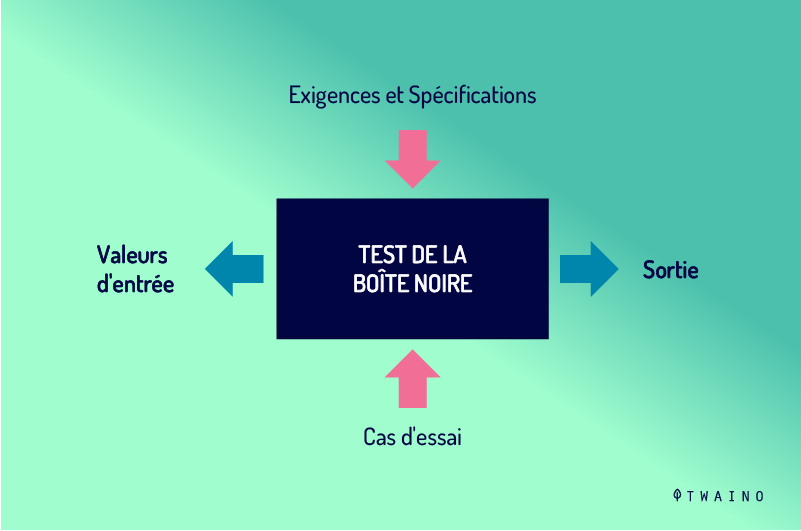
This testing methodology compares with White Box testing methods, where the operator resolutely takes the internal workings of the program into consideration.
Black-Box testing is a style of software testing that can be applied virtually to any level and type of testing.
3-1-1-1- Black-Box testing procedure
Because there are countless possible combinations of inputs, time sequences and states, it is virtually impossible to test certain software programs completely.
Among Black Box testing techniques, some focus on reducing the input space into groups whose subsets are individually examined by the testers.
Thus, during Black Box testing, the following will be examined:
- Segmentation by equivalence class, where the software data is subdivided into equal portions so that all sections are tested.
- Limit values to check for errors in input values.
- Parameters for bugs.
- Etc.
Black-box testing essentially involves organizing and adjusting software inputs without reference to the source code. The aim is to determine, assess and verify the outputs.
3-1-1-2- Advantages of Black-Box testing
Black-Box testing forces the tester and his team to assess the software from an external point of view, substituting themselves for the user. This separates the tester socially and critically from the code developer.
In this way, the tester’s objectivity in handling the software (the box) is ensured. What’s more, as the test is remote from the application development, its execution and the results obtained from it can enable the software to be explored in a way not envisaged by its designer.
Furthermore, a Black Box test requires no preparation prior to execution, unlike White Box tests where configuration, instrumentation or code analysis steps precede each test.
With Black Box, the operator just tries to use the application.
3-1-2- Other Black Box IT applications
Still in computing, there are many other references to the Black Box.
- In cryptology, Black Box theory is used in the design and processing of cryptographic algorithms, but also to understand and study the capabilities of an invisible or unknown adversary;
- BlackBox (in Unix computing) is a stacked window manager for X Window System platforms;
- BlackBox Component Builder for software development in Component Pascal;
- Project BlackBox, the Sun Modular Datacenter prototype;
- And many more.
3-2- The Black Box of digital marketing
The homonymy with the Black Box in the marketing world usually boils down to the simple fact that companies don’t exactly know and master how marketing works. And when the term is combined with the qualifier digital, the mystery is at its height, like an authentic Black Box.
Of course, this is just a figment of the imagination, as the Black Box is purely imaginary. In fact, digital marketing techniques are described exhaustively on the Internet.
To grasp digital marketing in the best possible way, all you need to do is research the subject online and do your homework.
It’s not difficult to open the imaginary box of digital marketing. And for good reason: altruistic digital marketers don’t hide their work. Better still, many of them are committed to developing and sharing the best of their knowledge, in order to differentiate themselves from the competition and prove their mastery of the profession.
What’s more, it’s quick and easy to hire a digital marketing agency. So, if there’s an aspect of your digital marketing that concerns you in any way, they’ll be happy to explain it to you.
Furthermore, while digital marketing as a discipline is not a Black Box, some of the tools it employs for its operation are technically Black Boxes.
Indeed, for laymen, and even for marketers, the way certain campaign management software works is unknown. The user-advertiser only has access to the graphical campaign programming interface, and even the tool’s optimization procedures are barely visible.
3-3- Black Box applications outside software
In addition to the technical context of computer programming and data mining products, the term Black Box is also used in countless areas of life. The exact meaning of the term and its prerogatives differ from sector to sector. Even so, the concept of the Black Box always bears the emblem of the mysterious.
3-3-1- In telecommunications
Here, Black Box is used to designate the resistance connected to a telephone line to prevent the telephone company from detecting or intercepting, with its equipment, a call that has been picked up.

Source: black-box.co.in
3-3-2- In the entertainment world
More specifically in the world of cinema, Black Box is equivalent to peripheral equipment specially dedicated to a particular function. In television and theater, Black Box refers to any empty, unfurnished studio.

Source: estonianworld.com
3-3-3- In the transportation sector
In the transport sector, the term Black Box is used to designate a device for automatically recording data relating to the operation of transport equipment:
- Maritime ;
- Rail ;
- Road ;
- Air, etc.
This Black Box recording technology is specially designed to withstand:
- Weathering ;
- Fire ; Water
- Water;
- High-gravity impacts;
- High-pressure environments;
- Etc.
The only reason the device is so resistant is to protect and preserve the data stored inside it.
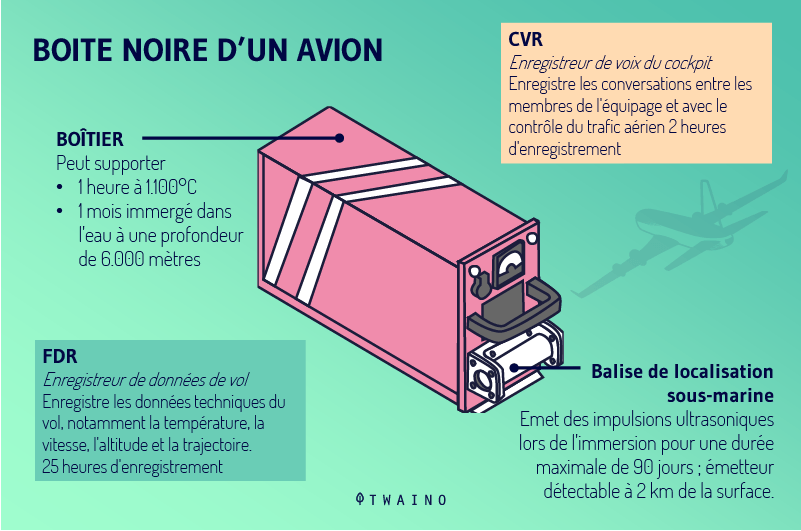
In addition to its various features, the Black Box normally transmits a signal that often helps locate the transport device in the event of a disaster. You’ve probably already heard of the Black Box, which provided information on the circumstances of a plane crash.
Although Black Box systems theory visualizes the aircraft itself as a Black Box, in the transport context, only the box is so named.
3-3-4- In financial terms
In financial terms, the Black Box is a computerized trading system whose operating rules are difficult to access.

Moreover, in economics, according to the famous neoclassical theory, the company is a Black Box. As the Black Box principle stipulates, we’re only concerned with what goes in and what comes out.
3-3-5- In the human sciences
In psychology and philosophy, the behaviorist school sees the human mind as a Black Box system.
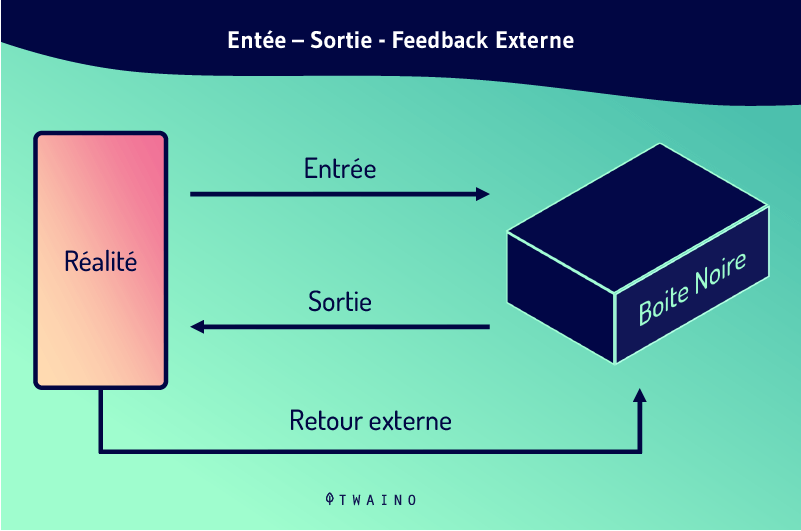
In these disciplines, this theorization is applied to the conscious being who reacts to stimuli from his environment, and whose internal mechanisms behind this response we do not wish to deal with.
3-4- Black box and e-commerce
In e-commerce, the black box plays an important role in protecting the confidentiality of customers and transactions. When a customer places an order, he or she provides sensitive information such as name, address and credit card details.
All this information is processed inside the black box, which ensures that sensitive data is not exposed to unauthorized third parties.
The shopping cart and the order are also part of the black box. When customers add items to their shopping baskets, this information is stored in the black box until the order is placed. This ensures that prices and stock availability are up to date and accurate when the customer is ready to finalize the order.
The customer’s region and language are also taken into account in the black box. Depending on the customer’s location, rates and shipping options may vary. In addition, the black box ensures that the website is displayed in the appropriate language for the customer, thus providing an optimal experience.
The black box also manages customer accounts. It stores customers’ login details, delivery addresses and order histories. This ensures that customers can easily access their account and track their order history.
Partnership and Space are also important in the black box. Partners can access certain parts of the black box to manage orders and inventory. However, confidential customer details are protected and not disclosed to partners.
To sum up
The concept of the Black Box is not new. It’s a multi-disciplinary, ubiquitous concept that can be applied to anything and everything.
In the context of Google search, the Black Box refers to the barriers the search engine has erected around its algorithms and actions as a company.
However, the technical inaccessibility of search algorithms does not prevent the proper SEO optimization of websites. That’s why the search giant has made a point of describing the main factors governing the indexing and ranking of websites in the SERPs.
What do you think of Google’s Black Box?
Do you know of any other areas where the Black Box has been applied?
Don’t hesitate to share your opinion in the comments.
See you soon!